Debian/Ubuntu manual HTTPS configuration
If you are changing your domain from HTTP to HTTPS, you will unlink the browser extension of all the users. Before changing the domain, you must ensure that all the users have a copy of their private key to recover their account.
Pro tips: In order to download their recovery kit, users can follow this dedicated guide
Passbolt debian and ubuntu packages currently supports the configuration of nginx. It comes with a default configuration that supports:
- Serve passbolt on port 80 (http)
- Serve passbolt on port 443 (https)
On this context ‘manually’ means that the user will provide the SSL certificates, this is the main difference with the ‘auto’ method where Let’s Encrypt will issue the SSL certificate for you.
This manual method is often useful on private network installations with private CA where the system admin issues a new private SSL certificate and uploads it to the passbolt server. It is also a method often used with self-signed SSL certificates for test installations.
On this example we will assume the user is generating a self-signed certificate on the passbolt server.
Generate the SSL certificate
While connected to your passbolt instance you can generate a SSL certificate in the following way:
openssl req -x509 \
-newkey rsa:4096 \
-days 120 \
-subj "/C=LU/ST=Luxembourg/L=Esch-Sur-Alzette/O=Passbolt SA/OU=Passbolt IT Team/CN=passbolt.domain.tld/" \
-nodes \
-addext "subjectAltName = DNS:passbolt.domain.tld" \
-keyout key.pem \
-out cert.pem
This command will output two files: key.pem and cert.pem. Identify the absolute path where these files are located as you will need them in next steps.
Of course, replace -subj values with your own. It is important to set your passbolt FQDN in both CN and subjectAltName. In this way, you will be able to import the generated certificate in your operating system keychain and make your self-signed domain trusted in your browser.
You can use an IP address instead of a domain name for your self-signed certificate. If you do that, replace DNS with IP in subjectAltName.
Install or reconfigure passbolt
If you don’t have passbolt installed please check on the hosting section for more information on how to install passbolt on debian.
If you have already installed passbolt then you want to execute the following command to start the configuration process for SSL:
sudo dpkg-reconfigure passbolt-ce-server
You most likely want to say ‘NO’ to the mariadb/mysql setup question and go for the nginx setup
You should select 'YES' for the nginx setup:
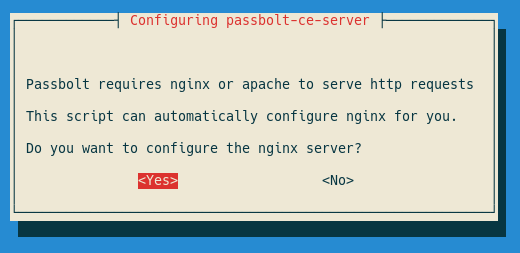
Choose ‘manual’ for the SSL setup method:
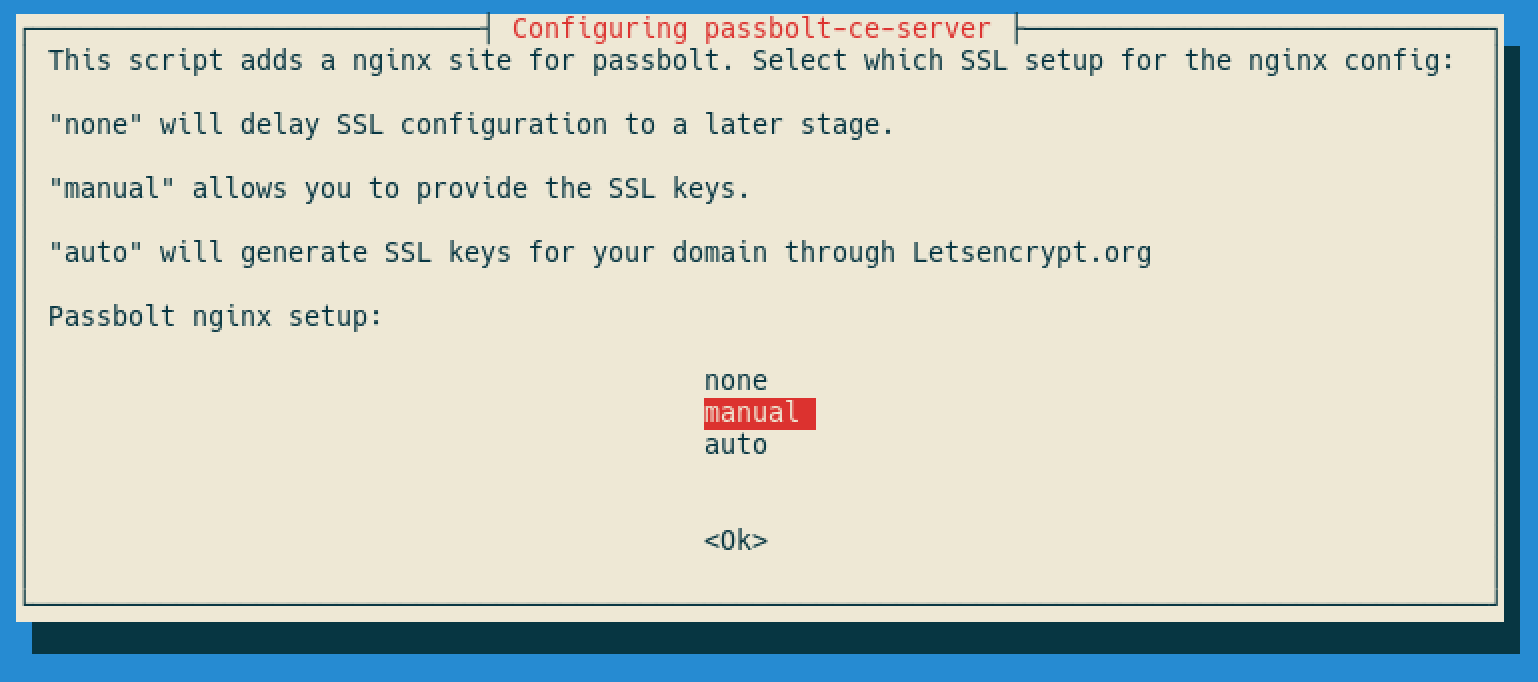
Provide the domain name you plan to use for your passbolt server. On this example and as we are using a self-signed certificate the domain name is not as important as if you are planning to use a proper SSL certificate. In the later escenario DNS domain name and SSL domain name must match.
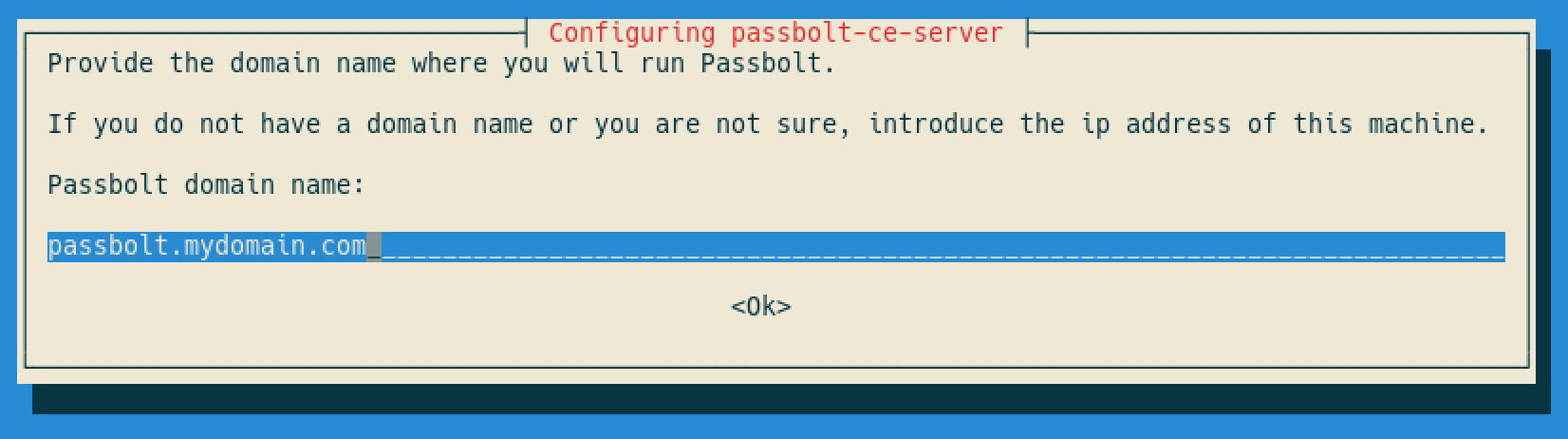
Provide the full path of the SSL certificate you created on previous steps: cert.pem
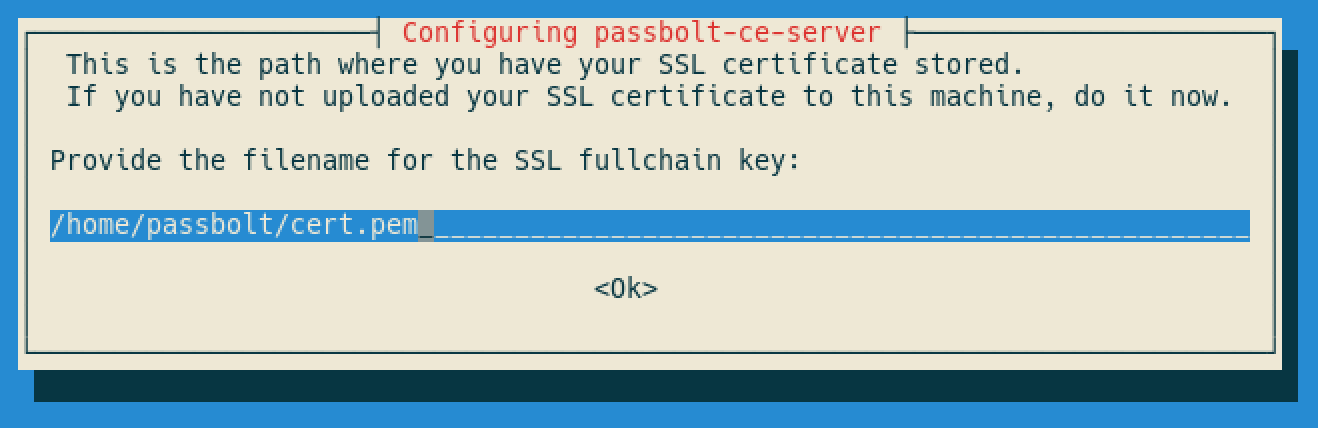
Now provide the full path of the SSL key: key.pem
Keep in mind that you might need to add DNS records to reach your domain on your local network or in a public DNS provider.
If everything goes fine you should see a final message that points you to finish passbolt configuration:
Reload nginx after finish the reconfigure to use the SSL configuration.
sudo systemctl reload nginx
Finally, ensure fullBaseUrl value in /etc/passbolt/passbolt.php starts with https://.
And that’s it you should be able to reach your server on the domain you specified.