How to Synchronize Users and Groups from a Directory
Overview of LDAP Integration in Passbolt
The LDAP connector will send an invitation email to all the users matching your configuration during a synchronization. If you are simply testing it, make sure not to perform an actual synchronization (use simulate sync instead), or disable the cron job to send emails first.
Passbolt Pro offers a user directory synchronization feature (LDAP connector) that allows administrators to synchronize users and groups from an external directory into Passbolt.
Currently, two directory types are officially supported:
- OpenLDAP
- Microsoft Active Directory
The integration works by periodically syncing the list of groups and users (along with group memberships) from the directory to Passbolt, minimizing manual user management. If certain actions cannot be automated (e.g., a protected user cannot be deleted), Passbolt will send email notifications or require admin intervention.
Key Considerations and Limitations
Important Notes
- One-way sync: Passbolt treats the directory as the source of truth for creating/updating users and groups, but some actions in Passbolt (like manual deletions) are considered higher priority and will not be overridden by sync.
- No delegated authentication: LDAP integration does not support login via directory credentials. Users must authenticate using their Passbolt account (private key + passphrase or configured SSO).
- No nested groups: Only direct group memberships are supported. Nested groups (groups within groups) are not.
- Email invitations: Synced users receive an email invitation to activate their account. When testing, use the Simulate Sync option to avoid unintended invitations.
- Username/Email requirements: Each LDAP user must have a unique email. If emails are not available, use the
Use email prefix/suffixoption with a defined domain. - Admin user and group manager: Assign a Default admin for performing syncs and a Default group manager for managing new groups.
Setup Best Practices
General Configuration Steps
-
Prerequisites
- Ensure the PHP LDAP extension is installed (
php-ldapon Debian/Ubuntu). - Ensure the server can connect to the LDAP/AD server (firewall/VPN as needed).
- Ensure the PHP LDAP extension is installed (
-
Enable the Directory Sync plugin
- Go to Organisation settings → Users Directory
- Toggle the Enable switch.
- Complete all required fields and run a successful connection test.
-
Enter LDAP connection settings
- Directory Type:
Active DirectoryorOpenLDAP - Domain (AD only): e.g.
mydomain.localorexample.com - Server URL:
ldap://198.163.0.1:389(unencrypted or with STARTTLS) orldaps://ldap.example.com:636(implicit TLS) - Bind Username & Password:
e.g.,CN=readonly,DC=mydomain,DC=local - Base DN:
- AD:
DC=mydomain,DC=local - OpenLDAP:
dc=example,dc=com
- AD:
- User Path & Group Path (optional):
e.g.,OU=MyUsers,OU=MyGroups - Object classes (OpenLDAP only):
- Users:
inetOrgPerson - Groups:
groupOfUniqueNames
- Users:
- Default Admin:
A Passbolt admin user responsible for sync actions. - Default Group Manager:
The user assigned to manage synced groups.
- Directory Type:
-
Filtering options
- Groups/Users parent group:
Restrict sync to subtrees. - Custom LDAP filters:
e.g.,(memberof=CN=PassboltUsers,OU=Groups,DC=example,DC=com) - Enabled users only (AD only):
Syncs only enabled accounts. Recommended for production. - Sync operations toggle:
Disable create/update/delete individually as needed.
- Groups/Users parent group:
-
Save and test
- Click Save settings.
- Run Simulate synchronize to preview changes.
- Review for expected users/groups and issues before a real sync.
-
Run first synchronization
- Once verified, click Synchronize.
- Review the report for actions taken and errors.
-
Verify results
- Check the Passbolt UI for imported users/groups.
- New users will be in "invitation pending" status.
💡 Tip: Never run sync as root. Use the correct web server user.
For example, on Debian/Ubuntu:
su -s /bin/bash -c '...cake directory_sync...' www-data
Setup guide
This guide explains how to configure the LDAP connector through the UI. More complex configurations (for example custom field mapping in openldap or multiple server synchronisation.) can be achieved via file-based configuration. File based configuration and support is part of Enterprise services, please contact us for more information.
Activate the plugin
The plugin is deactivated by default. You need to activate it to be able to use it. While logged in as an admin, click on the administration menu item in the top menu, and then click on "Users Directory".
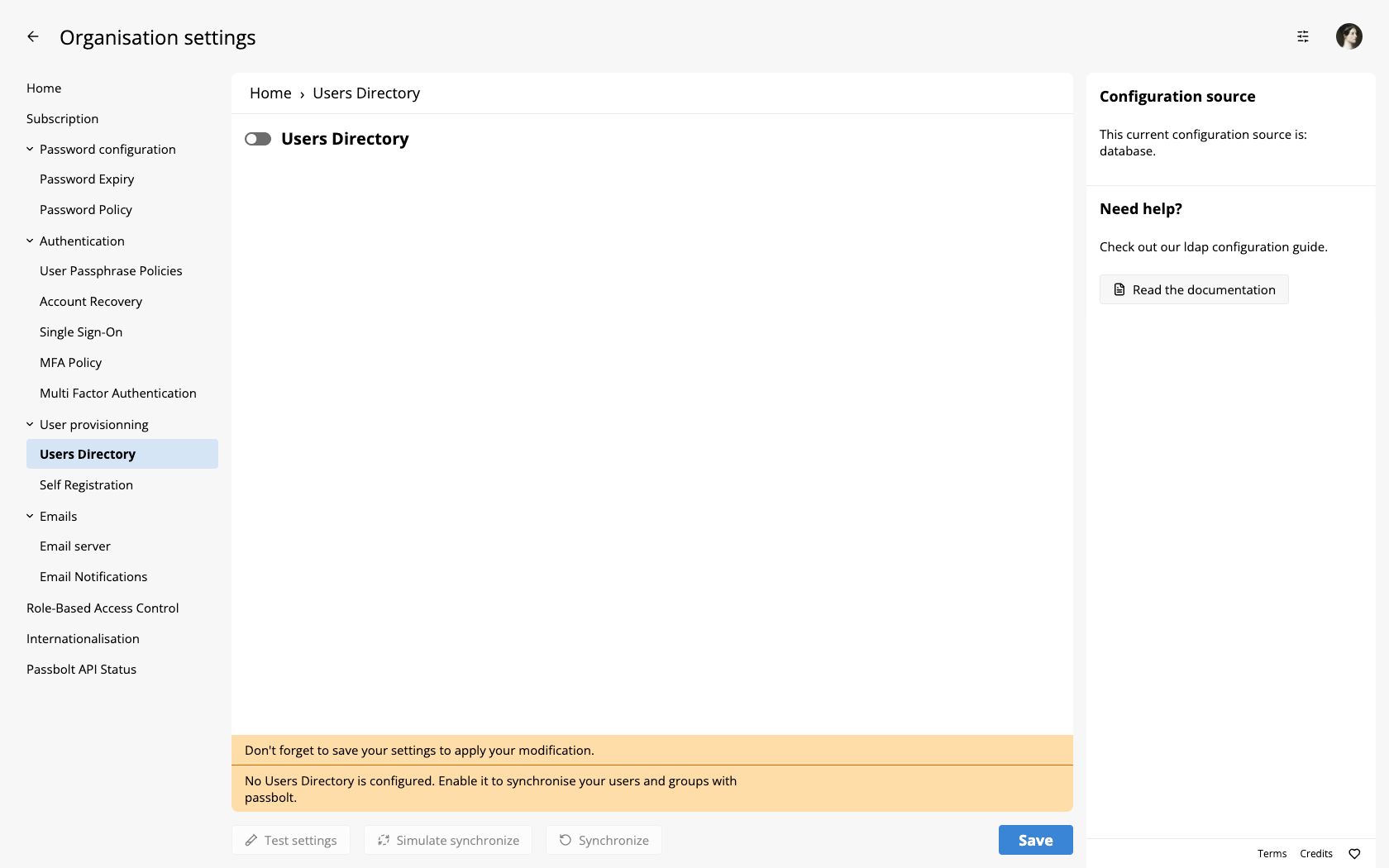
Click on the switch next to "Users Directory" to enable the plugin.
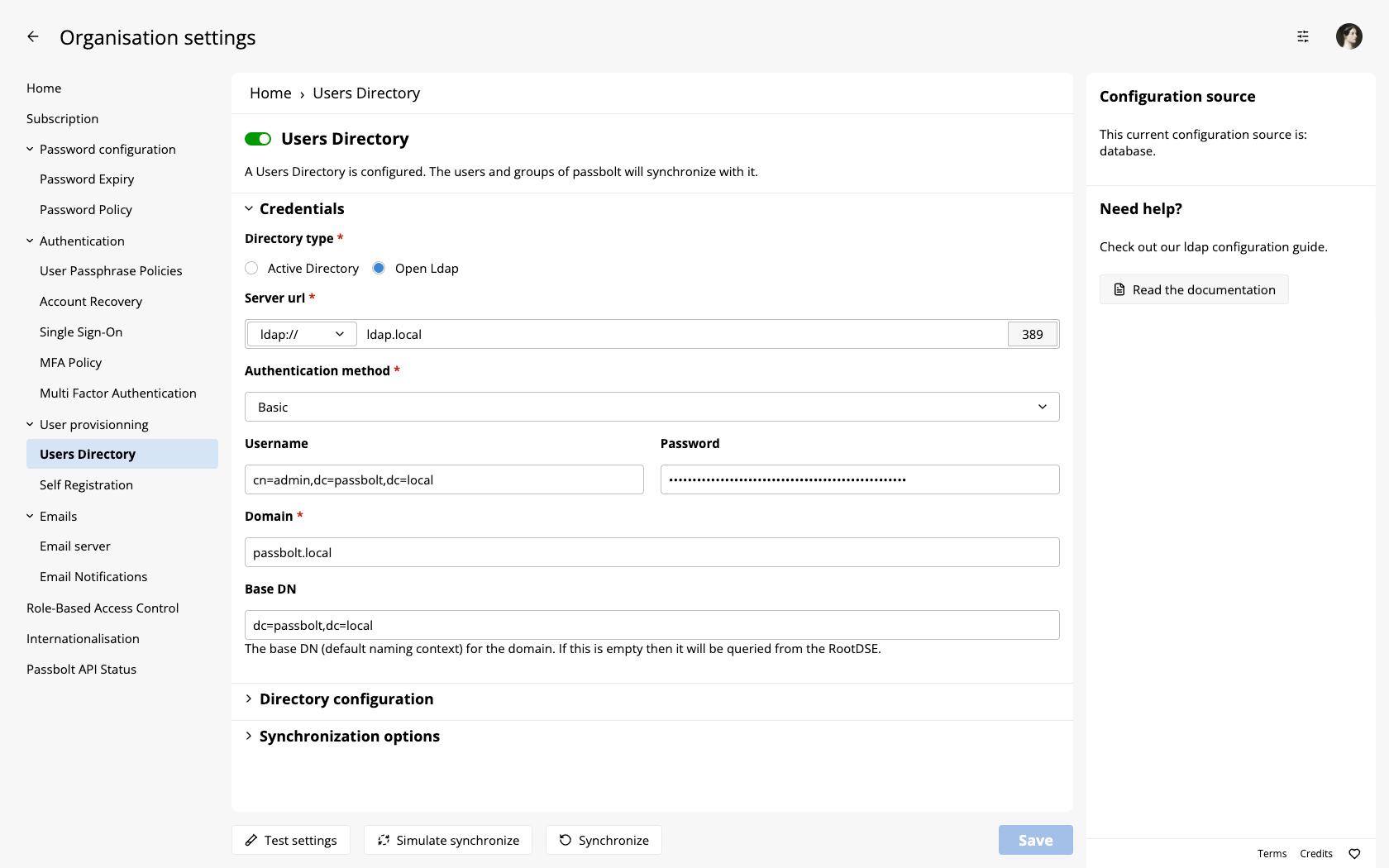
You will need to fill the configuration parameters with your connection details before you can save the settings and actually activate it.
Save configuration
Once the configuration is entered, do not forget to save it by clicking on the "Save settings" at the top. The configuration will be saved only if passbolt managed to connect to your directory. If not, it will display an error message.
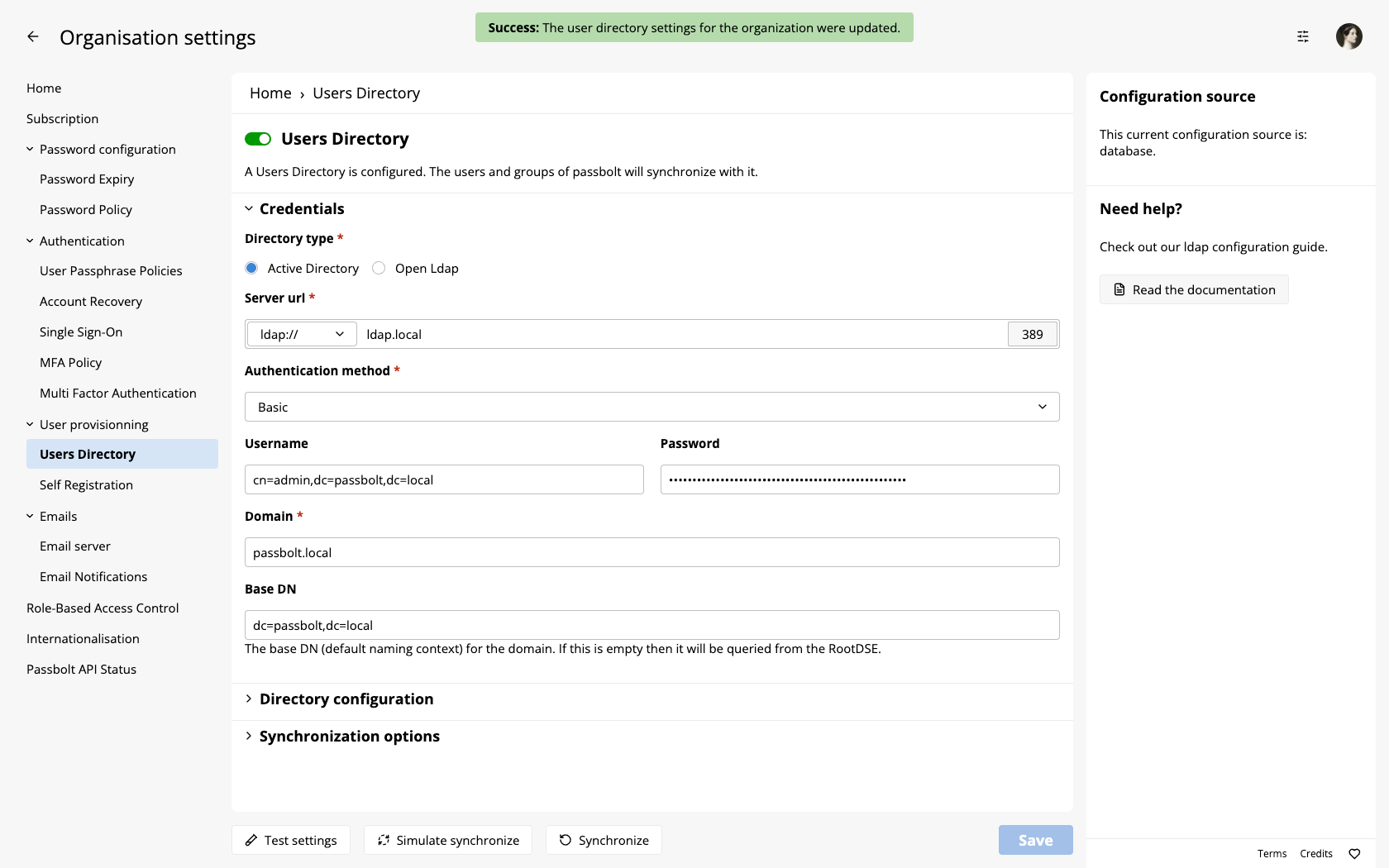
Test configuration and simulate sync
Once the settings have been saved, the buttons "Simulate synchronize" and "Synchronize" at the top have become clickable.
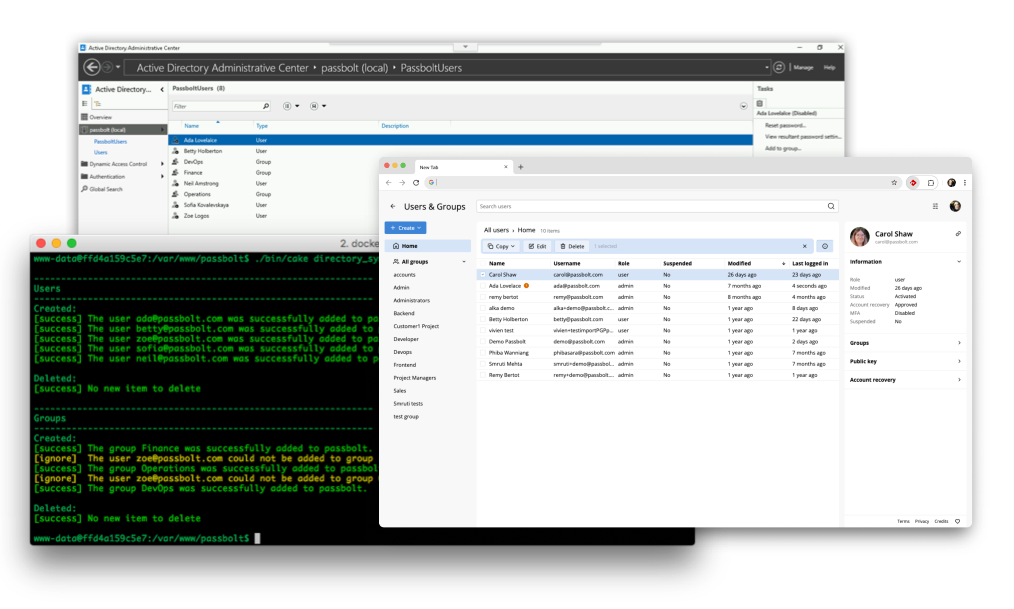
Before we actually do a real synchronization, we will first simulate one. Click on "Simulate synchronize" and wait a few seconds. Once the simulation is complete, a report such as the one below will be displayed.
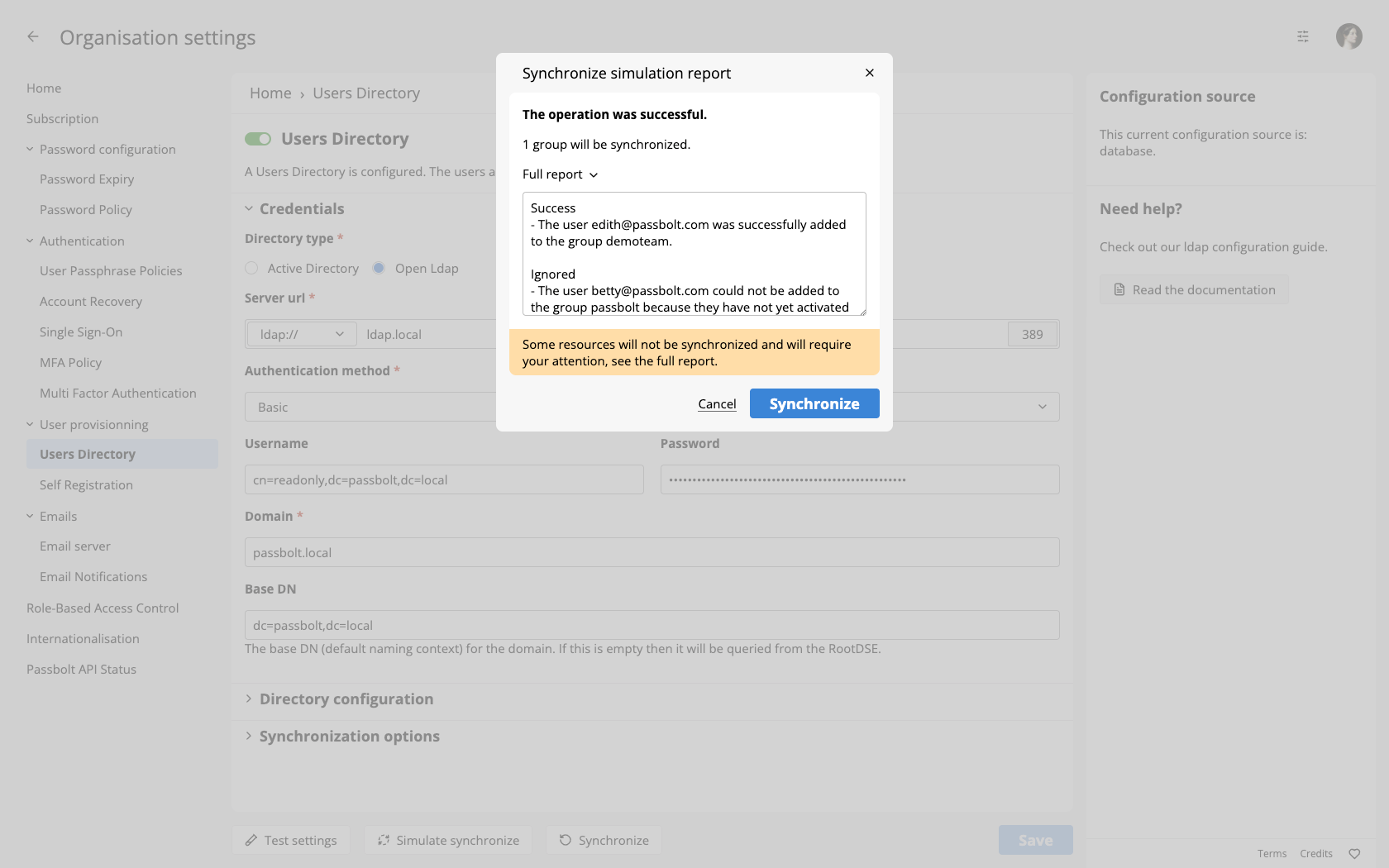
In this report, you will be able to see what will actually happen when you will synchronize your directory for real. You will also be able to take corrective measures before an error actually happens.
First synchronization
To do the first synchronization, repeat the same process as above. Only, click on "Synchronize" this time. A similar report to the one that was displayed during a simulate will appear and let you know what happened exactly.
User synchronization example workflow
When an user is created in LDAP, they are imported in Passbolt using synchronization.
If you delete this user in Passbolt, he will remain present in LDAP but won't be added back to Passbolt on next synchronization.
If you want to re-sync this user with LDAP, manually re-create him in Passbolt then run synchronization. Passbolt synchronization tool will automatically recreate the link in Passbolt database.
If you delete this user in LDAP, he will be deleted from Passbolt on next synchronization.
Going further
How to synchronize my directory automatically?
If you want to automate the synchronization, you (or the person in charge of hosting) will need to setup a cron job.
Configure LDAPS (implicit TLS)
If your configuration doesn't run out of the box with LDAPS, you can refer to the LDAP with TLS (SSL) configuration documentation in order to adjust your config or throubleshoot your issue.